Instead of patronizing this potentially unwanted application, immediately run a full scan of the PC using a legitimate security product. Anti-malware application are known to combat rogue programs like XP Anti-virus 2011. On this page is our suggested removal tool that was tested to remove counterfeit applications. Download, install and update the database before running a full scan on the system. Remove all detected threats and if possible run a scan while the computer is in Safe Mode.
Screen Shot Image:
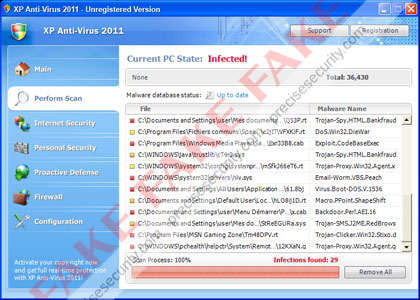
Damage Level: Medium
Systems Affected: Windows 9x, 2000, XP, Vista, Windows 7
XP Anti-Virus 2011 Removal Procedures
Manual Removal:1. Press Ctrl+Alt+Del on keyboard to stop process associated to “XP Anti-Virus 2011″. When Windows Task Manager opens, go to Processes Tab and find and end the following process:
(random characters).exe
2. You need to update your installed antivirus application to have the latest database.
3. Thoroughly scan the computer and any detected threats must be removed. If removal is prohibited, it is best to quarantine the infected item. Manually locating and deleting of malicious files should also be performed. Please see files below that are related to XP Anti-Virus 2011 Virus.
4. Registry entries created by XP Anti-Virus 2011 must also be remove from the Windows system. Please refer below for entries associated to the rogue program. [how to edit registry]
5. Exit registry editor.
6. Get rid of XP Anti-Virus 2011 start-up entry by going to Start > Run, type msconfig on the “Open” dialog box. A windows containing System Configuration Utility will be launched. Go to Startup tab and uncheck the following Start-up item(s):
(random characters).exe
7. Click Apply and restart the computer.
XP Anti-Virus 2011 Removal Tool:
In order to completely remove the threat from a computer, it is best to download and run Malwarebytes Anti-Malware. Sometimes, Trojans will block the downloading and installation of MBAM. If this happens, download it from a clean computer and rename the executable file before executing on the infected computer.
Using Portable SuperAntiSpyware:
To thoroughly clean a computer, it is best to do a separate scan of another security program so that other infected files not detected by anti-virus application can be remove as well. Download and run SuperAntiSpyware Portable Scanner.
Technical Details and Additional Information:
If XP Anti-Virus 2011 is installed on the computer, it will begin to display fake alerts as an scare tactics to mislead victims:XP Anti-virus 2011 Firewall AlertMalicious Files Added by XP Anti-Virus 2011:
XP Anti-virus 2011 has blocked a program from accessing the internet
Internet Explorer is infected with Trojan-BNK.Win32.Keylogger.gen
Private data can be stolen by third parties, including credit card details and passwords.
%AllUsersProfile%\[random]
%AppData%\[random]
%UserProfile%\Local Settings\Application Data\.exe
%UserProfile%\Templates\[random]
%Temp%\[random]
XP Anti-Virus 2011 Registry Entries:
HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “%1″ %*’
HKEY_CLASSES_ROOT\.exe\shell\open\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CLASSES_ROOT\.exe\shell\runas\command “(Default)” = ‘”%1″ %*’
HKEY_CLASSES_ROOT\.exe\shell\runas\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CLASSES_ROOT\exefile “Content Type” = ‘application/x-msdownload’
HKEY_CLASSES_ROOT\exefile\shell\open\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CLASSES_ROOT\exefile\shell\runas\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CLASSES_ROOT\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “%1″ %*’
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “C:\Program Files\Mozilla Firefox\firefox.exe”‘
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “C:\Program Files\Mozilla Firefox\firefox.exe” -safe-mode’
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “C:\Program Files\Internet Explorer\iexplore.exe”‘
HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = ‘exefile’
HKEY_CURRENT_USER\Software\Classes\.exe “Content Type” = ‘application/x-msdownload’
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon “(Default)” = ‘%1′ = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “%1″ %*’
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “(Default)” = ‘”%1″ %*’
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CURRENT_USER\Software\Classes\exefile “(Default)” = ‘Application’
HKEY_CURRENT_USER\Software\Classes\exefile “Content Type” = ‘application/x-msdownload’
HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon “(Default)” = ‘%1′
HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\<random 3 letters>.exe” /START “%1″ %*’
HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “IsolatedCommand” = ‘”%1″ %*’
HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “(Default)” = ‘”%1″ %*’
HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “IsolatedCommand” – ‘”%1″ %*’
HKEY_CLASSES_ROOT\.exe\DefaultIcon “(Default)” = ‘%1′
No comments:
Post a Comment